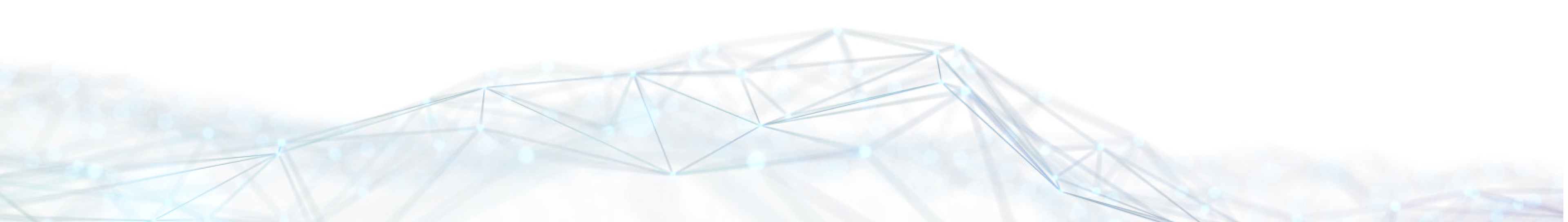
On March 31, 2022, China's cybersecurity authority AQNIU officially released the "Panorama of China's Cybersecurity Industry (Ninth Edition)" hereinafter referred to as the "Panorama"). The "Panorama" is positioned to show the overall ecosystem and development status of China's cybersecurity industry and representative manufacturers in sub-fields. Since its launch, it has been widely concerned and recognized by the industry.
With its core technical strength in industrial control security, HollySys Information Security Research Institute was overwhelmingly selected into two major fields of computing environment security and industrial control security, and four sub-fields of trusted computing, industrial control security detection and protection, industrial control security management, and industrial control security services, fully covering the industrial control security field.

Trusted Computing
Secure and Trusted PLC Control System
Based on the trusted computing 3.0 system, it is mainly composed of three parts: the main security controller, security engineer station, and security management platform. The main security controller adopts a dual-system architecture, a domestic operating system and a real-time system; the security engineer station has added digital certificate-based identification on the basis of the original engineering password to realize two-factor authentication; the digital certificate for communication encryption/decryption is generated by the security management platform, and the encryption algorithms approved by the State Password Administration Committee Office are used to encrypt/decrypt the communication data in the data communication stage.

Industrial Control Security Management
Industrial Network Security Management Platform
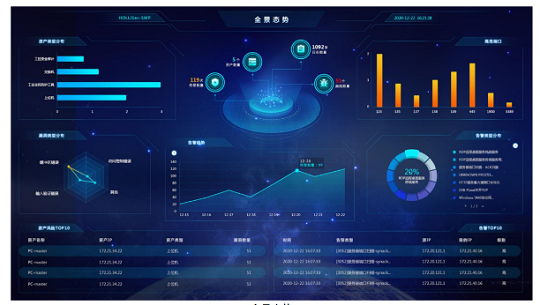
By collecting data from various IT and OT devices in the industrial control system, it can provide real-time analysis and visual display of data to perceive abnormal behaviors and events in the industrial network. At the same time, it performs centralized performance status monitoring and security policy management for terminal equipment such as host computers, servers, controllers, network equipment, and industrial control security equipment in the industrial network. It can provide a basis for decision making, realize closed-loop industrial information security disposal, and ensure the safety and reliability of industrial production.
Industrial Security Isolation and Data Exchange System
Based on the design concept of complete security architecture, it takes the lead in improving the concept of industrial control security isolation, adopts a number of exclusive technologies, and supports file synchronization, database synchronization, and video protocol transmission identification, and air gap. Moreover, it provides a variety of different levels of hardware to meet the needs of different working conditions, and the enhanced sales license to ensure system security to the greatest extent.

Terminal Security Protection System
It is an industrial host terminal protection product developed and launched for industrial control networks, which can provide host trusted computing capabilities, whitelist policy control, host access control, host security hardening, and operation monitoring. With the trusted computing technology at its core, it builds an autonomous defense system to make the computing results consistent with expectations and the computing process measurable and controllable, which can identify the malicious components entering the system promptly and develop the immunity for the computer information system.
Situational Awareness System for Industrial Network Security
It can carry out overall security correlation analysis of various types of data from the industrial control network in production control area I, production control area II and management information regional network, obtain the security risk and situation of plant-level networks, and realize comprehensive monitoring of external and internal security attacks.
Industrial Control Security Detection and Protection
Industrial Network Security Audit System
In addition to supporting more than 20 common industrial control protocols, it exclusively allows parsing HollySys' DCS control system protocol and provides custom interfaces for other private protocols that are not open to the public. The audit system also integrates an intrusion detection module and has built-in rules for detecting the vulnerabilities of equipment from various domestic and foreign industrial control manufacturers, thus detecting various external attack threats promptly and ensuring the secure operation of the industrial control system.

Industrial Intrusion Detection System
The industrial intrusion detection system has a rich built-in vulnerability exploitation rule base, covering multiple levels of operating systems, industrial control application software, industrial control equipment, and industrial control protocols. The rule base is classified by operating system, industrial control software & equipment manufacturer, and industrial control protocol. Moreover, it can provide rule templates that are easy to understand and deploy from the perspective of users, which effectively avoids the abuse of intrusion rules and improves intrusion detection efficiency.

Intelligent Detection System for Industrial Network Security
The product can be flexibly configured to collect asset information actively or passively, adapt to corresponding inspection strategies based on various on-site business scenarios and compliance guidance requirements, and fulfill functions like configuration verification, vulnerability scanning, business auditing, network intrusion detection, and host-side malicious virus detection. It allows on-site customers to efficiently and accurately complete the system security assessment by providing visual and intuitive process scanning, as well as clear and detailed report content.

Industrial Control Security Services
HollySys Information Security Research Institute has a security service team composed of senior experts, which has obtained the qualification certificate for "Capability Assessment of Information Classified Security Protection and Security Construction Service Agencies" and that for "Information Security Services" issued by the First Research Institute of the Ministry of Public Security of PRC. It has been authoritatively recognized for its capabilities of service management, service technology, and service process, and can provide users with integrated solutions for industrial control security, including services like security integration, risk assessment, and security O&M.
In the future, HollySys will continue to pursue technological innovation and deep exploration into the field of industrial control security, jointly improve its layout in network information security with industry partners based on its technical advantages in the field of industrial control, and continue the building of a complete cybersecurity ecosystem.